IP: 3.149.249.127
Your ISP: Analyzing ...
Your location: Analyzing ...
Analyzing ...
- Log in
- Registration
- Servers
- Pricing
- Download
- Guard Suite
- About us
- Blog
- Social Media
- Privacy policy
- Terms of service
- Contact form
IP: 3.149.249.127
Your ISP: Analyzing ...
Your location: Analyzing ...
Analyzing ...
Published at: 2023-11-02 08:00
The LockBit ransomware group, closely monitored by our Dark Web Team, has announced its latest high-profile victim: The Boeing Company.
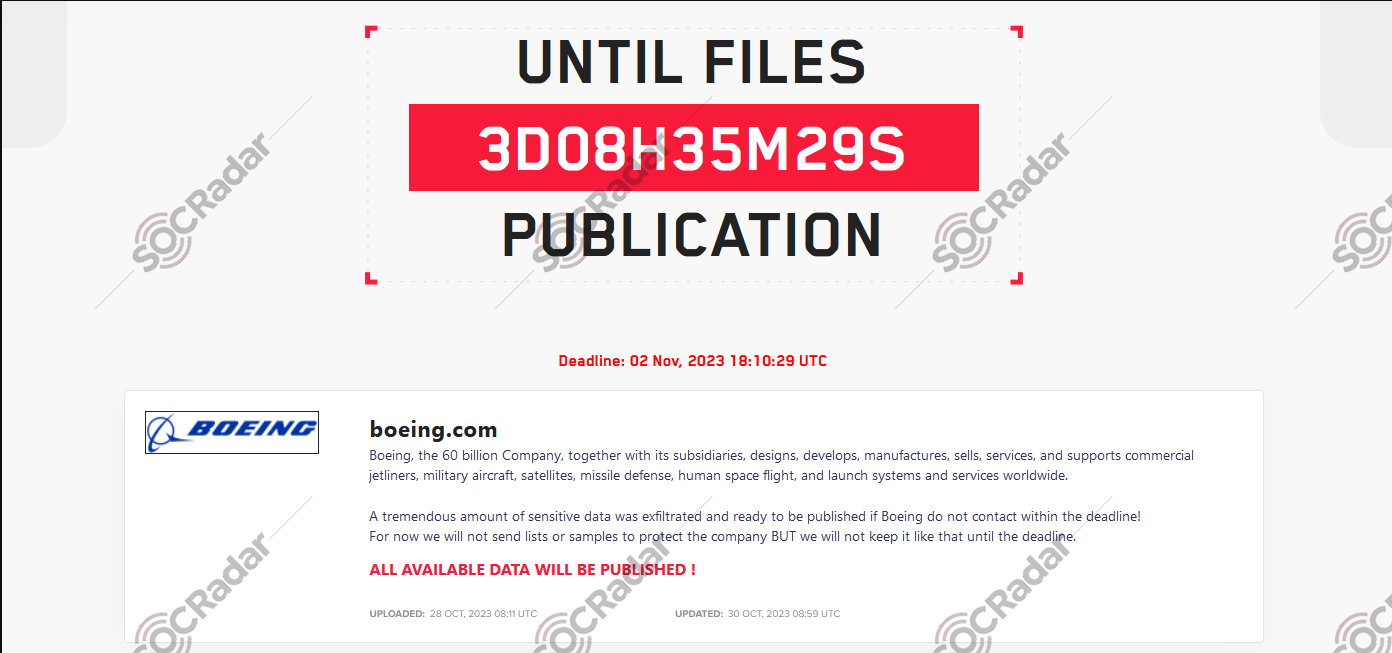
Print of the leaked post in the Hacker forum
According to the group's dark web announcement, LockBit has allegedly exfiltrated a massive cache of sensitive data from Boeing. Hackershave set a deadline of November 2 for Boeing to reach out, threatening to release the data if their conditions are not met. What's notable is their decision to withhold specifics about the data volume and to abstain from sharing sample data, purportedly to safeguard Boeing's interests. Boeing, a leading aerospace company, manufactures both commercial and military aircraft. The company also designs and produces helicopters, defense systems, missiles, satellites, and launch vehicles.
LockBit 3.0 is a Ransomware-as-a-Service (RaaS) group that continues the legacy of LockBit and LockBit 2.0. From January 2020, LockBit adopted an affiliate-based ransomware approach, where its affiliates use various tactics to target a wide range of businesses and critical infrastructure organizations.
LockBit has been highly active in deploying models such as double extortion, initial access broker affiliates, and advertising on hacker forums. They have even been known to recruit insiders and make contests in forums for recruiting skilled hackers; such expansionist policies have attracted numerous affiliates, have victimized thousands of entities, and continue their malicious acts.
The most successful RaaS group operating since 2019. The group is continuously evolving nad is highly active in deploying models such as double-extortion and initial access broker affiliates.